Security is the most important part of any enterprise application. So we need to secure SOA Production environment secure and make Jdeveloper communicate with that secure environment.
In this blog I’ll show you how to import certificate into weblogic and jdev and make it accessible over https.You can take the certificate from any trusted CA but that incur some extra expense.For testing and development purpose you can use self signed certificate else you can download the signed certificate from a CA which is free of cost, will show you the link in steps later.So prerequisite is your SOA 11.1.1.5 env is ready with Admin server which contains SOA managed server, just follow the steps and you are done!
At first open a command prompt and set exactly the same JAVA_HOME which your weblogic server is using.For that just run <fmw_home>\user_projects\domains\base_domain\bin\setDomainEnv.sh or setDomainEnv.cmd. Check the java –version to recheck once again and issue the below commands.In all cases you can use your own alias name and keystore name.I created my own certificates directory(can be at any location) and change the path to the same.
1. Generate Private Key pair using keytool
keytool -genkeypair -alias myserver -keyalg RSA -keysize 2048 -validity 365 -keystore shrikIS.jks -storepass welcome1
During key pair generation it will ask for some details onscreen and provide the same as per your wish.But for Prod environment your prod server URL would be the CN value.You can go ahead with any arbitrary value for testing purpose,after this command you can find shrikIS.jks created.
2. Generate CSR to be submitted to CA
keytool -certreq -v -alias myserver -file serverCert.csr -keypass welcome1 -storepass welcome1 -keystore shrikIS.jks
after this command you will find serverCert.csr file created in your directory.Just open that in notepad and copy the content like below sample,
-----BEGIN NEW CERTIFICATE REQUEST-----
MIICtTCCAZ0CAQAwcDELMAkGA1UEBhMCSU4xCzAJBgNVBAgTAkhSMRAwDgYDVQQHEwdHdXJnYW9u
MRMwEQYDVQQKEwpzaHJpa3dvcmxkMQswCQYDVQQLEwJJVDEgMB4GA1UEAxMXU2hyZWVrYW50YSBS
b3ljaG93ZGh1cnkwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQCrurewhMtAxY/BGRPn
sWQANSIFqIprGDaCOz/YH3XAcUguPg7lUTkE8o6tRfT6vMrMSai2/zg8Cc9dwbNaTtRoJu15qAHq
6Ta6SjvQ4VeIwAP8T2BNnrHn+GQuo7E0ef0hNHuvVcsLoZy6dBlXIc/WBn869xUKt84+ZZ79cII8
VenWFvJXi1f8NxitkjKRzbOydFOVwOza8Lo90V7Tn/DkV2OHpL9bjLnWJhLT5ZGwxhnqne79tJbV
VTZepndjhuz0JEc4DjjS2TZqsT7q4zdXM0+5HwJDOxvqjEegfSewfwPlXGSLHhOSA1s6fsEQtmZ9
h7IGSC5TJQnoXyOyxz4lAgMBAAGgADANBgkqhkiG9w0BAQUFAAOCAQEAVbIrPKGA5d6CPzXfB50S
GE4c/1OAH+qx+cv0ZzulgnfuPdKaVWzqJDc13UquCBjl/8fKevASgTtmw420JVZX6teOiCUtH06n
tO1EIT/Ti53D5KIDCQhRosMl54OjBzYwfejTDXbjoOHtKHzQo9Wi8W5sl4dd5jAp1BP/PBbfxaBS
LLPbzSRxcQKTszpeE6ekFSaKzll1CnuBhCydjXMOf6rKFOD7s1vT5uN4+GFRjtXGUlzYqcKfCTgj
OBS/MfSru4IIZtweyXJUhGPCvLaVWyq0VQ+3x4TLXDrw1579MtDunuTaJiysk1bRc1Tjrhy/hmlP
txsGAdmwrduApovnHA==
-----END NEW CERTIFICATE REQUEST-----
You need to send this CSR to a CA who will give you root certificate,sometimes intermediate certificate and signed certificate(public key).Go to http://www.getacert.com/signacert.html.
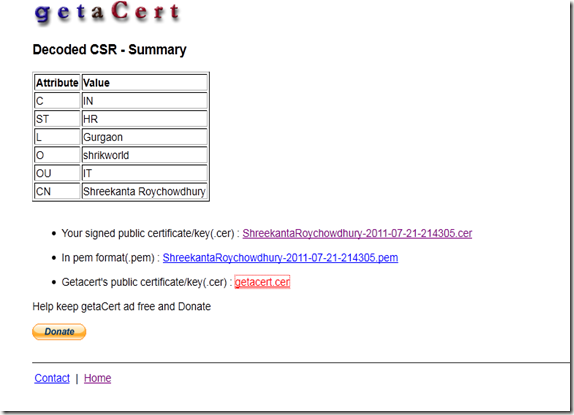
So here in the blank section copy paste your CSR content and click submit. After that you reach the below screen,
From this screen download all two .cer files in same directory.
3. Import the getacert.cer file as RootCert as below,
keytool -import -file getacert.cer -alias RootCA -keystore shrikIS.jks -storepass welcome1
4. Establish Certificates Chain
Then you have to import the ShreekantaRoychowdhury-2011-07-21-214305.cer file , but remember here you have to give same alias name as you given while generating the private key pair at first step, to establish the certificate chain.
keytool -import -file ShreekantaRoychowdhury-2011-07-21-214305.cer -alias myserver -keystore shrikIS.jks -storepass welcome1
You should see ‘Certificate reply was installed in keystore’ message after executing the above command.
5. Create Trust Store
Now export the public key of your certificate and store it in a trust store by using below commands,
keytool -export -alias myserver -file server.cer -keystore shrikIS.jks -storepass welcome1
keytool -import -alias server -trustcacerts -file server.cer -keystore shrikTS.jks
After this you will find another keystore shrikIS.jks is created in your directory.
Download keytool-iui from http://code.google.com/p/keytool-iui/ to see or manage your keystore in a GUI interface, its pretty cool one,here are the screenshots for mine,
6. Configure Weblogic Server
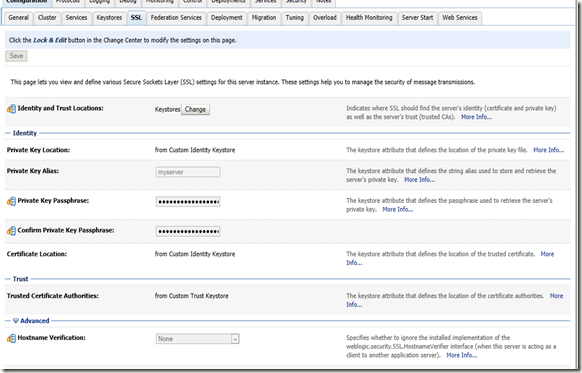
Now go the server tab of your weblogic console,
Click on Adminserver and keystore tab there after,
Change the keystore to Custom Identity and Custom Trust and provide the Identity store and trust store location with password. Give keystore type JKS.Now click the SSL tab and give the private key alias and password there,
Here in the Advanced section select Hostname verification to none (in Prod don’t do that) and select Client Cert Requested But not Enforced in Two Way Client Cert Behavior: section dropdown list.
Then go the General tab and enable SSL port ,
Thant’s All ! you are almost set , secure all the managed server in same fashion.
Now restart the Server and try to open the console giving https and SSL port. You will find the certificate information in the browser,
You can view that certificate is issued to you and issued by getacert.
7. Configure Jdeveloper 11.1.1.5
Now you have to configure Jdeveloper to communicate with secured weblogic server.
For that open the jdev.conf file under <Jdev_Home>\jdeveloper\jdev\bin directory to check the Java location,
Now go to the <JDK_Folder>\jre\lib\security directory and copy your server.cer file here that you created in step 5.We need to import that to cacerts by below command
keytool -v -import -file server.cer -keystore cacerts
give the default password changeit.
Now open the Jdev and go the preference section under Tool –>HTTP Analyzer –>HTTPS Setup.Here give the Identity and Trust store location and password as below,
Now in the Appserver Connection in Resource Palette select your SOA server configuration and select Always use SSL as below and test the same.
You should get all success here and that completes the SOA Environment Security.






7 comments:
Excellent post shreekanta
ShreeKanta,
Thanks for a simple and excellent blog. Can you please list me the steps to consume a .pfx certificate in soa somposite?
Thanks,
Jai.
Thanks for a simple and excellent post. Can you please list me the steps to consume a .pfx file in soa composite?
-Jai.
If you want to replace keytool with a GUI tool then you can also use CERTivity.
http://www.edulib.com/products/keystores-manager/
It can handle different types of keystores (JKS, JCEKS, PKCS12, BKS, UBER, Windows) and digital signatures.
Hi Sreekantha,
Thank you for such a nice blog on security.
I tried to implement it, however i am facing issue while starting the managed server.
Error is:
javax.net.ssl.SSLKeyException: [Security:090482]BAD_CERTIFICATE alert was receiv
ed from 127.0.0.1 - 127.0.0.1. Check the peer to determine why it rejected the c
ertificate chain (trusted CA configuration, hostname verification). SSL debug tr
acing may be required to determine the exact reason the certificate was rejected
.
at com.certicom.tls.interfaceimpl.TLSConnectionImpl.fireException(Unknow
n Source)
Kindly help me.
Regards,
Shailmala
Is the keystore is same for Admin and Managed server?
If its different then try to import the admin server key onto managed server truststore and try to bounce.
Thanks,
Shreekanta
Hi Shreekant,
Thanks for the useful information. If weblogic and Jdeveloper are in different machine, then i see issues while connecting via https even after following these steps. It says SSL handshake failure.
DO you have any inputs to this?Please share.
Thanks
Smitha
Post a Comment